It lets more network traffic through! That’s what promiscuous mode (or p-mode) does for the network card. It allows additional network traffic to the rest of the endpoint. What exactly do I mean by that and why does this need to happen sometimes? Here’s a quick overview of p-mode in both a traditional context for understanding and Skytap’s approach to providing an option to leverage certain aspects of this feature.
First, the “what”: Network cards have MAC addresses. Network connected devices like virtual machines (VM), computers, mobile phones, etc. send and receive traffic labeled with this MAC address. By design, all other traffic is filtered out (dropped) instead of going on to be processed by the device. Sounds great, right!? Your device doesn’t have to process the undesired traffic.
Second, the “why”: Now that we know the what of p-mode, let’s think about the why. Sometimes, there is a desire not to drop the other traffic. This is the traditional promiscuous mode. Why would you want to let all that network traffic be seen by the device? Won’t it mean a lot more processing of data it may not need? There are some motivators for bringing on this extra workload to your VM including packet sniffing and nested virtualization where the endpoints on that nested hypervisor need to communicate out:
- PACKET SNIFFING is used to gain insight into network traffic. Packet sniffers read all of that traffic and have various use cases like troubleshooting, simulating threats for training, or showcasing intrusion protection solutions.
- NESTED VIRTUALIZATION is hosting virtual machines within an endpoint that is already running on a hypervisor. The endpoint has a network card (unique MAC) and any virtual machines on it would have their own network card. P-mode is not necessary in general to nest, but if the underlying endpoints on it need to communicate out, this is the use case. Traffic will need to pass through in order for that nested VM to have a chance to review network traffic instead of getting dropped by the endpoint. This requires an extra check box in Skytap. To solve this, review the article Enabling nesting hypervisors.
Skytap Promiscuous Mode
Skytap’s promiscuous mode provides a way to action on packet sniffing and nested virtualization use cases, but to a different extent of the traditional sense. For packet sniffing it is important to note port spanning (mirroring) is not a means to capture in Skytap. You can use a nested hypervisor with its own network to use inline/bridge methods for passive packet inspection. Inline/bridge devices can exist on the Skytap network; all packet data from client devices that transit these devices can be monitored from these devices. The network card on your hypervisor with p-mode enabled is able to send and receive traffic using a forged mac address from one of the nested VMs on that hypervisor. See the diagram below.
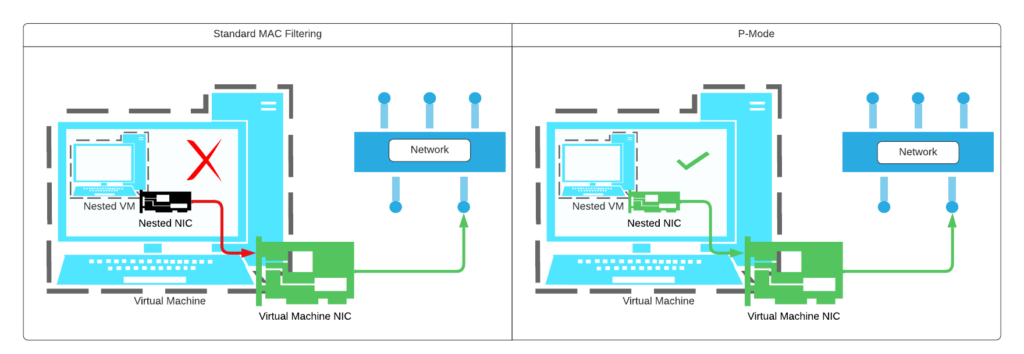
We have identified a couple good reasons to use promiscuous mode. Because of the type of behavior this feature has, misconfiguring could result in loops. It is not available in Skytap without request and authorization. If the use case was approved and your user has been granted the promiscuous mode permission by an administrator in the account, you simply select a radio button in the network settings of a powered off VM.
For most of us, allowing additional traffic to be processed isn’t a benefit. When the need to call on for more information and more insight of what traffic is out there, p-mode is the first step to take and thankfully it’s a simple one. For more information about promiscuous mode or help with your use of Skytap, contact our team of experts today.
Skytap team members that contributed to this blog: Randy Courtright – Cloud Solutions Architect at Skytap
Randy Courtright – Cloud Solutions Architect at Skytap
 Marcus Bowman – Site Reliability Engineer at Skytap
Marcus Bowman – Site Reliability Engineer at Skytap
